Introduction
Over the past decade, we have been seeing a change in how IT services are delivered in several organizations and how they used traditional terminologies to accomplish employees’ work requirements. Ever so often these technologies get replaced by advanced ones as per the demands and needs. Modern business revolves around data, and now every work term is connected with data, so it is important to keep that data secure or use it in secure business environments. Now enterprises need something that brings them all the necessary things to their place with reliable security. Gartner proposed a new term named a secure access service edge that helps organizations run their businesses from anywhere with a secured environment by enabling networking and security capabilities under one roof. By reading this solution paper users can easily understand the SASE model and its benefits that address the current challenges in IT firms.
What is SASE?
Secure access service edge also known as SASE unites networking with security and provides secure access to all users from anywhere. SASE redefines the traditional perimeter, replacing on-premises systems with integrated cloud services. It identifies the valid user when granting access to data and applications. It also enables organizations to offer more security services as business needs grow. SASE combines network security functions (such as secure web gateway, CASB, firewall as a service, and zero trust network access), with WAN capabilities to support the dynamic secure access needs of organizations.1
Gartner first describes this in the August 2019 report. The Future of Network Security in the Cloud and expanded upon in their 2021 Strategic Roadmap of SASE Convergence.1
Secure Access Service Edge provides all the networking as well as security features under one roof. SASE is called as future of cloud architecture as companies are familiar with cloud structures, application adoption, and infrastructure migration. Several organizations are using cloud security solutions as an add-on to on-premises security to address current security problems.
Fig. 1: Secure Access Service Edge
Why do we need it?
SASE is becoming necessary as our working culture is changed, delivering safe access to business resources from everywhere with enforced security policies. It increases productivity and reduces risk by authorizing users to improve access to their data, applications, and services. As we know security perimeters are updated by corporate infrastructure to wherever people work on whichever devices but the aim is to provide access to necessary data and services without disturbing productivity or putting users’ information at risk.
UK’s National Cyber Security Centre and the US Cybersecurity and Infrastructure Security Agency(CISA) issued a joint advisory in April 2020 at the outset of the pandemic warning of various COVID-19-related attacks aimed at remote access infrastructure and remote workers’ accounts.[1]
Remote users need fast, easy-to-use, and more secure access to their applications when they are not working on a trustworthy environment or devices. SASE supports an integrated network and security infrastructure to manage security using a unified programmable policy and it provides a secure working environment with secure access.
As we know during the pandemic several organizations and remote workers went through several problems while managing data and security. It becomes a little hectic while granting access to data and applications and at the same time managing the security perimeters. SASE resolves all these problems and manages to provide secure access from everywhere by providing cloud, data, and threat protections.
Architectural Approach:
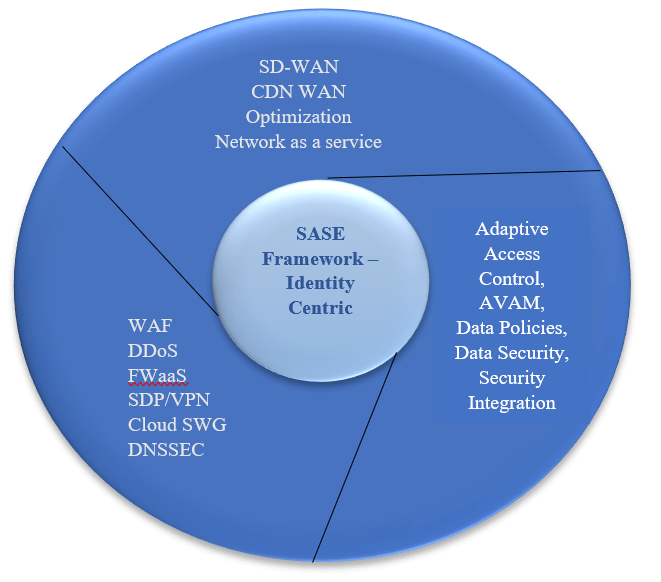
Fig. 2: SASE Framework
SASE defines an architecture we use today to improve our tomorrow. It supports a cloud-delivered architecture that unifies networking and security services to protect applications, users, and data from any location. It provides cloud-native microservices from a single platform architecture that enables both networking and security services. Starting with cloud access security brokers, software-defined wide area networks, virtual private networks, firewalls as a service, and secure web gateways, it is confirmed that we are in a cloud-native security environment. It enables software-defined perimeter with zero trust network access by replacing the traditional procedures.
By 2025, one-third of new SASE deployments will be based on a single-vendor SASE offering, up from 10% in 2022.[2] Gartner proposed that SASE capabilities are delivered as a service dependent on the identity of the attributes, and enterprise security. The SASE architecture supports some key capabilities which are given below.
Identity Driven: SASE enables context-based decisions to grant security and access permissions when the policy enforcement process takes place. Identity enables network security services in the SASE platform which makes automatic policy enforcement possible. It will identify the network or the resources through the attributes like the user, device, and location to permit authorized access.
Support All Edges: SASE creates one platform where remote users or organizations can get access to a network and security. It is a single comprehensive platform for the whole network that covers all edges, all applications, and all traffic.
Globally Distributed: Distributed SASE architecture easily accommodates traffic and minimizes interruptions to remote users as it ensures that users or enterprises are getting all the networking and security capabilities and delivering the best experience from all edges.
Cloud-Native: SASE architecture matters as it offers cloud-native microservices that can scale out as per requirements. This architecture provides some important cloud functionalities like availability, elasticity, self-maintenance, and adaptability to build an environment so that users can manage their work from everywhere.
Benefits of SASE
Secure access service edge is a combination of networking and security services that provides several benefits to the cloud network. Various techniques and terminologies are used to manage secure transactions in the cloud system structure. It delivers security services in a consistent and integrated way to support edge computing and digital business transformation. Some benefits are given below.
Cost Effective: It enables network security in the cloud and helps decrease capital expenditure for on-premises infrastructures. It eliminates the backhauled traffic flows and enables cost-effective transport choices. It provides enforcement of security policies which automatically replaces the hardware cost.
Reduced Complexity: Traditional legacy solutions are replaced with consistent and integrated extendable security solutions that strengthen the security postures of organizations and it enables end-to-end configuration of network and network security infrastructure which automatically helps to reduce the complexity.
Centralized Policy Enforcement: Centralized policy enforcement helps to improve the security parameters and provides proper security solutions, it supports cloud-based simplified policy management that enables organizations to manage the cloud applications and endpoint protection irrespective of the perimeters.
Improve Security and User Experience: It supports network transformation, cloud transformation, and optimal user experience due to these qualities users can easily access the systems from everywhere. It has all notions of application and user monitoring availability, leading to the best user experience.
Increased, Optimized Performance: It enhances performance and decreases latency by eliminating the traffic flows to optimize the user experience. Consistent access control policies enable secure access to internet appliances through a global network infrastructure optimized for high capacity, low latency, and high availability.
Enables New Digital Business Scenarios: It creates a converted technology platform that enables unified policy enforcement that helps to migrate the cloud unconstrained by traffic flows and supports a scalable architecture that enables digital transformations. Security as a service approach provides rapid growth and low-cost adoption of technology improvements.
Enables Least Privilege Access: It uses zero-trust principles that offer secure access to private applications in the public cloud, as it enforces authentication of all resources and users that restricts access to any resource based on the defined policy and mitigates lateral movements of threats from the connected network system.
[1] https://www.usa.gov/federal-agencies/cybersecurity-and-infrastructure-security-agency
[2] https://blogs.gartner.com/andrew-lerner/2022/09/30/single-vendor-sase/?_ga=2.96759775.1902877956.1667216342-1064354753.1655713748