Enhancing Online Security by Understanding Web Application Firewalls (WAF)
DataNudge
March 2023
The growing number of cyber dangers provides a huge challenge to web applications in today’s interconnected digital world. SQL injection, cross-site scripting (XSS), and distributed denial-of-service (DDoS) attacks are all threats to websites and web-based services. Organizations rely on a powerful security solution, a Web Application Firewall (WAF), to reduce risks and secure critical data. In this blog article, we’ll delve into the realm of Web Application Firewalls, learning what they are, how they work, and why they’re so important in protecting web applications.
What is Web Application Firewall (WAF)?
A Web Application Firewall or WAF is a security solution that guards web applications against malicious actions and cyber threats. It serves as a barrier between web servers and the internet, filtering and monitoring incoming and outgoing web traffic. WAFs, as opposed to traditional firewalls, explicitly target web application layer traffic, making them particularly effective in detecting and mitigating application-layer threats.
How Does It Work?
Web Application Firewalls analyze and filter web traffic using a variety of ways, allowing only legitimate requests to reach the web application server. It is a critical component of modern cybersecurity systems, providing defense against various web application assaults. WAFs offer organizations a strong defense against known and developing risks by utilizing rule-based filtering, positive or negative security models, behavioral analysis, machine learning, and AI. Organizations can improve the security posture of their online applications and protect sensitive data from unscrupulous actors by adopting a WAF. WAFs commonly employ the following methods:
1) Rule-based Filtering
WAFs rely on rule-based filtering to identify and prevent known attack patterns. WAFs use established rules to detect distinct attack signatures, patterns, or regular expressions often linked with different sorts of assaults. SQL injection, for example, is one of the most common web application vulnerabilities. An SQL injection attack happens when an attacker injects malicious SQL code into the input fields of a web application, modifying the database and potentially gaining unauthorized access to sensitive information.
By analyzing incoming request parameters and comparing them to a set of specified criteria, a WAF can guard against SQL injection. If the WAF identifies any malicious SQL instructions or patterns in the request, it will block or sanitize it, preventing the attack from being successful. WAFs’ preconfigured rules are updated on a regular basis to reflect new attack signatures and patterns identified in the field. This contributes to the WAF’s ability to successfully identify and block the most recent attack strategies, offering a proactive defense against known threats.
2) Positive and Negative Security Models
Web application firewalls can work with either a positive or negative security model. These models specify how the WAF handles incoming web traffic and determines what is permitted or prohibited. In a positive security approach, the WAF only allows expressly approved requests and rejects all others. This means that all requests must fulfill the security policies’ specified criteria. A positive security architecture has the advantage of enforcing a stringent whitelist approach, guaranteeing that only known legitimate requests are let through. However, careful setting is required to ensure that valid requests are not mistakenly banned.
In a negative security approach, on the other hand, the WAF allows all requests by default, except those classified as malicious based on specified rules. This strategy employs a blacklist approach to stop known attack patterns. Because the emphasis is on recognizing and blocking malicious requests allows for greater flexibility and easier implementation. However, there is a risk of false positives, which occur when genuine requests are incorrectly classified as malicious and banned. Both positive and negative security models have benefits and drawbacks, and organizations must select the model that best meets their specific security needs and risk tolerance.
3) Behavioral Analysis
Advanced WAFs use behavioral analysis techniques to detect and prevent unusual or suspicious traffic patterns. Rather than depending entirely on predefined rules, these WAFs monitor user behavior, session data, and other contextual data for anomalies that may indicate an attack. The goal of behavioral analysis is to establish a baseline of normal behavior for users and apps. The WAF then analyses and compares incoming traffic to this baseline on a continuous basis. When the WAF identifies deviations from established patterns, such as unexpected user navigation, excessive requests, or unusual session activities, it can flag the traffic as suspicious and take necessary action, such as blocking or alerting.
This method is very successful at detecting threats that are undetected by typical rule-based filtering. A sophisticated attacker, for example, may devise an attack that does not trigger any known attack patterns yet exhibits strange behavior. A WAF’s behavioral analysis capabilities can aid in the detection of such attacks, adding an extra layer of defense.
4) Machine Learning and AI
Some current Web Application Firewalls use machine learning (ML) and artificial intelligence (AI) techniques to improve their threat detection capabilities. These technologies enable WAFs to analyze and learn from massive volumes of data, boosting their ability to detect and mitigate both known and emergent threats. ML-powered WAFs can spot abnormalities and detect previously unknown attack patterns by analyzing past traffic patterns. This enables them to detect zero-day attacks, which exploit vulnerabilities unknown to the general public, and give protection before patches or signatures are available.
Furthermore, ML and AI algorithms allow WAFs to adapt and evolve over time. They may learn from new attack strategies and adapt their rules and algorithms to remain effective against shifting threats. This adaptive functionality lowers the need for manual rule updates and allows the WAF to keep one step ahead of attackers.
In Comparison to Other Solutions, the Web Application Firewall
Web Application Firewalls are a critical security solution for safeguarding web applications. Other security technologies are available, but each serves a particular function and has unique characteristics. It should be noted that these tools are not mutually exclusive, and organizations frequently use a combination of security tools to develop a layered defense plan. Web Application Firewalls play an important role in this strategy by providing specialized protection against web application-specific assaults and assuring continuous web application security. Let’s compare WAFs with some of the commonly used security tools:
1) Network Firewalls
Network firewalls primarily focus on safeguarding network traffic at the OSI model’s transport layer (Layer 3) and network layer (Layer 4). They monitor and regulate network traffic depending on specified rules like IP addresses, ports, and protocols. Network firewalls, unlike WAFs, which operate at the application layer (Layer 7), have no visibility into the exact content or behavior of web applications. While network firewalls are important for network security, they do not offer the same level of protection against web application-specific assaults that WAFs do.
2) Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
IDS and IPS systems monitor network traffic for suspicious or malicious activities and can detect and alert prospective attacks. IPS solutions actively block or prevent malicious traffic based on established rules or anomaly detection, whereas IDS solutions passively analyze network traffic. IDS/IPS systems, on the other hand, are not specifically developed for web application security. They lack WAFs’ granular understanding of web application vulnerabilities and threats. WAFs provide web application-specific rule sets and protection methods, making them more successful in mitigating web application-specific assaults.
3) Web Vulnerability Scanners
Web vulnerability scanners are automated tools that check web applications’ code, settings, and server environments for vulnerabilities. They detect typical flaws like SQL injection, XSS, and vulnerable server setups. While vulnerability scanners are useful for detecting flaws, they do not safeguard online applications in real time. WAFs, on the other hand, offer continuous protection by actively screening and blocking malicious traffic, hence supplementing the vulnerability scanning process.
4) Web Application Testing Tools
Web application testing tools, such as penetration testing tools, are used to mimic attacks on web applications in order to detect flaws and vulnerabilities. These tools aid in the assessment of web application security by simulating the actions of possible attackers. While they are useful for detecting vulnerabilities, they do not provide continuous protection like WAFs. WAFs provide proactive defense in real time by actively blocking attacks based on established rules and behavioral analysis.
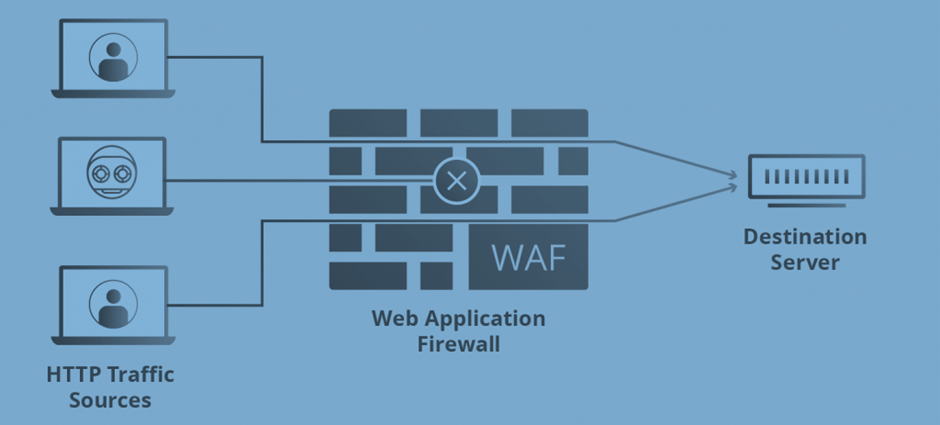
Benefits
Web Application Firewalls defend web applications by mitigating common attacks, enhancing security posture, guaranteeing regulatory compliance, and assisting organizations in combating DDoS attacks. Organizations may limit the risk of data breaches, instill consumer confidence, meet regulatory obligations, and keep their online applications available in the face of evolving cyber threats by installing a WAF.
1) Protection Against Common Web Application Attacks
WAFs are critical for safeguarding web applications from typical assaults like SQL injection, cross-site scripting, and remote file inclusion (RFI). These exploits exploit online application vulnerabilities to obtain unauthorized access, modify data, or compromise user information.
By analyzing request parameters and recognizing suspicious SQL code or patterns, WAFs with rule-based filtering can detect and stop SQL injection attempts. WAFs can detect and prevent XSS attacks by inspecting HTML replies for malicious script tags or input validation failures. By examining URLs and request parameters for suspicious file inclusion patterns, WAFs can detect and stop RFI attempts. WAFs dramatically minimize the risk of data breaches, unauthorized access, and other security events by screening and preventing these types of harmful requests.
2) Improved Security Posture
Implementing a web application firewall displays a proactive approach to security, which improves an organization’s overall security posture. Organizations that implement a WAF demonstrate their commitment to securing sensitive data while also maintaining the integrity and availability of their web applications. Customers and users are becoming more aware of security threats and require that their data be kept safe. Implementing a WAF increases consumer trust and confidence by demonstrating that their data is safe from prospective assaults. As a result, consumer loyalty increases and the organization’s reputation improves.
3) Regulatory Compliance
Many businesses, including finance, healthcare, and e-commerce, are subject to stringent security and compliance laws. The Payment Card Industry Data Security Standard (PCI DSS), for example, requires organizations that accept credit card transactions to maintain a secure environment. Failure to meet these criteria can result in hefty penalties, legal ramifications, and reputational harm. Web Application Firewalls help businesses meet these regulatory obligations. Organizations can impose security measures that conform with mandated standards and best practices by establishing a WAF. WAFs provide the essential defense against typical attacks and ensure that sensitive data is securely protected.
4) Mitigation of DDoS Attacks
DDoS attacks pose a substantial threat to web applications because they overload server resources with a torrent of traffic, rendering the site inaccessible to genuine users. WAFs can assist in reducing the impact of DDoS assaults by detecting and filtering out unauthorized traffic. DDoS assaults are detected and mitigated using a variety of approaches by WAFs. They can detect irregularities in incoming traffic patterns and distinguish between legitimate user requests and malicious traffic generated by bots or compromised devices. WAFs help preserve online applications’ availability and performance by blocking or limiting harmful traffic and ensuring that valid requests reach the server.
Conclusion
Web Application Firewalls are critical components of modern cybersecurity systems, providing defense against a wide variety of web application assaults. WAFs provide organizations with a strong defense against known and developing risks by utilizing rule-based filtering, positive or negative security models, behavioral analysis, machine learning, and AI. Organizations can improve the security posture of their online applications and protect sensitive data from unscrupulous actors by adopting a WAF.